Postgres Protocol and a Side Quest
· 1 min read
I was watching Heikki Linnakangas’s talk on the Postgres protocol. I wanted to follow along with and see the protocol in action for myself. I ran into a problem here: my ostgres server rejected all non secure connections. And with TLS enabled, I could not get wireshark to decode postgres protocol messages because of encryption.
Now, wireshark supports decoding TLS connections using a key log file. Looking through documentation I realized that there is no way for a client to log the TLS keys using psql. So the natural next step was to add that support and try to get that accepted upstream in postgres. Once I understood how this could be implemented, this became my side quest.
This patch was merged on 3rd April 2025. This allows a client to pass in a file name where psql will dump encryption secrets. Here is how to use it
psql "postgresql://user:pass@server:5432/postgres?sslmode=require&sslkeylogfile=/home/abhishek/foo.txt"
psql (18devel, server 17.4)
SSL connection (protocol: TLSv1.3, cipher: TLS_AES_256_GCM_SHA384, compression: off, ALPN: postgresql)
Type "help" for help.
postgres=>
And now when I configure Wireshark to read that file, it can successfully decode the postgres protocol
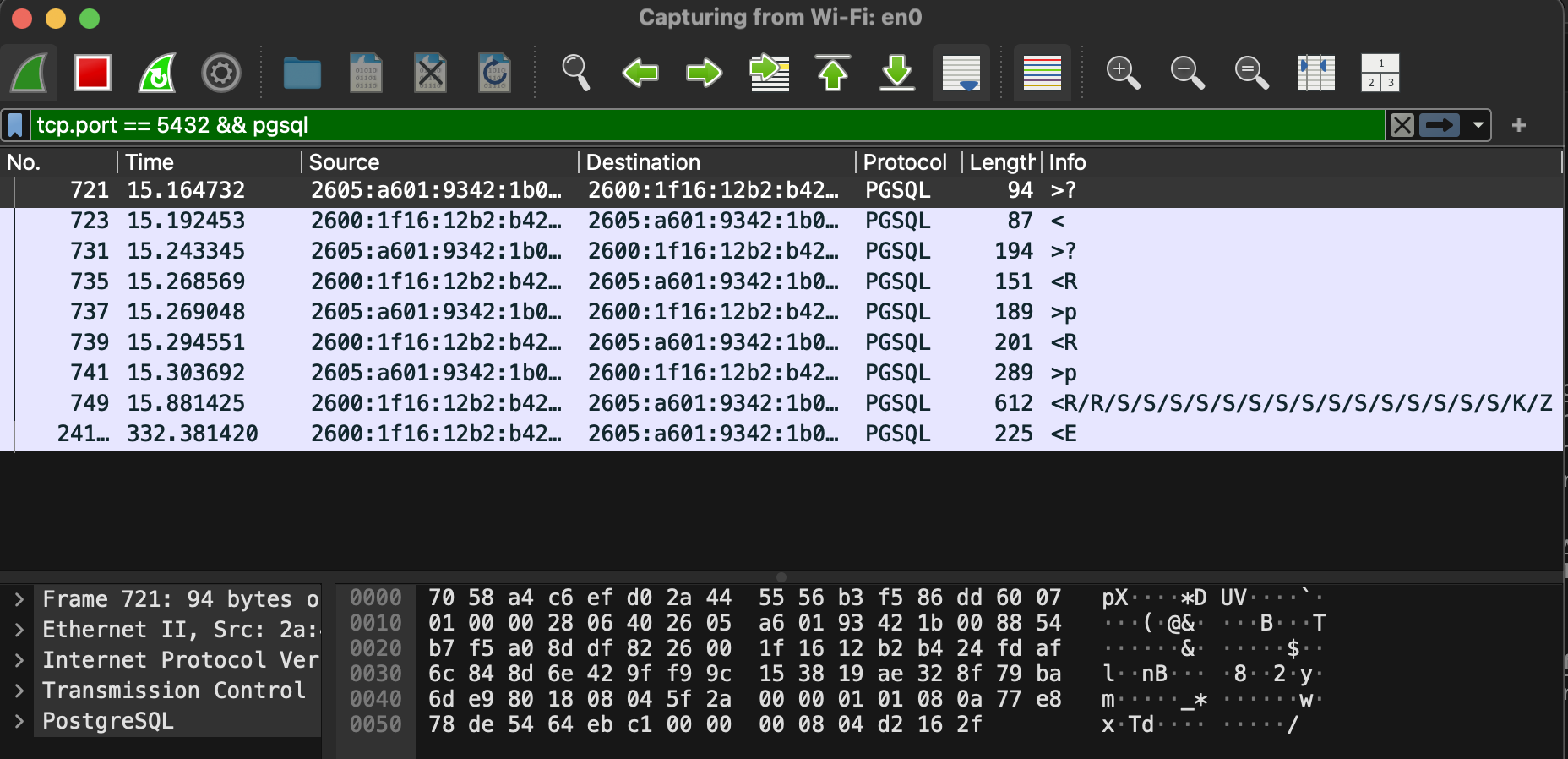
Happy debugging the postgres protocol!